Introduction
It’s Monday morning and you’re inundated with alerts from staff that the internet is down. By the time your IT team investigates the situation, staff and students are alerting you that their email has been disrupted. You and your team look at your firewall, flooded with traffic. That’s when you realize you’ve been hit with a distributed denial of service (DDoS) attack. It’s looking like a long day ahead.
In this post, we get technical, breaking down a DDoS attack, why it’s important to protect against them and how ORION can help.
In 2019, there were 200,000 attacks to educational services globally. In 2020, we’ve seen a 15% growth in DDoS attacks, and a 25% increase since the beginning of the COVID-19 pandemic. Multiple sources indicate the spike can be attributed to people being more reliant on online resources both for work and life.
What is a DDoS attack and how does it work?
A DDoS attack occurs when a hacker takes control of several computers and aims them at a single server, overwhelming that network with traffic and ultimately knocking it offline. DDoS attacks can be disruptive to teaching, learning, communication and other day-to-day operations relying on network-connected services that are vital to your organization’s sustainability. There are two major types of DDoS attacks: volumetric and state exhaustion. A volumetric attack is like a traffic jam clogging up the highway, preventing regular and, preferably, vital traffic from arriving at its desired destination. In a state exhaustion attack, it’s like someone trying to talk nonsense to you so you cannot process others who are actually trying to say something important.
Earlier this year, ORION experienced one of the largest DDoS events that has ever taken place on our network. It started with a “High Usage Alert” on ORION’s DDoS Threat Protection detection dashboard, indicating that one of the colleges on our network was being flooded with illegitimate traffic. The following reports will take us through the process our cybersecurity experts went through as they identified, managed and mitigated the incident.
In Figure 1, below, the DoS Alert Summary Report gives us basic information on what IP was being targeted in this particular incident, which institution the IP belonged to, the top identified misuse type and the impact the traffic was making. We can also visualize the traffic graphically and in terms of bps (bits-per-second) and pps (packets-per-second). This is important because it helps us to understand the potential impact of the attack on the target. In network security, and particularly in reference to DDoS, network traffic is measured in both bps and pps When a large DDoS attack occurs, like the one demonstrated here, both bps and pps levels are indicative of traffic that is unusual.
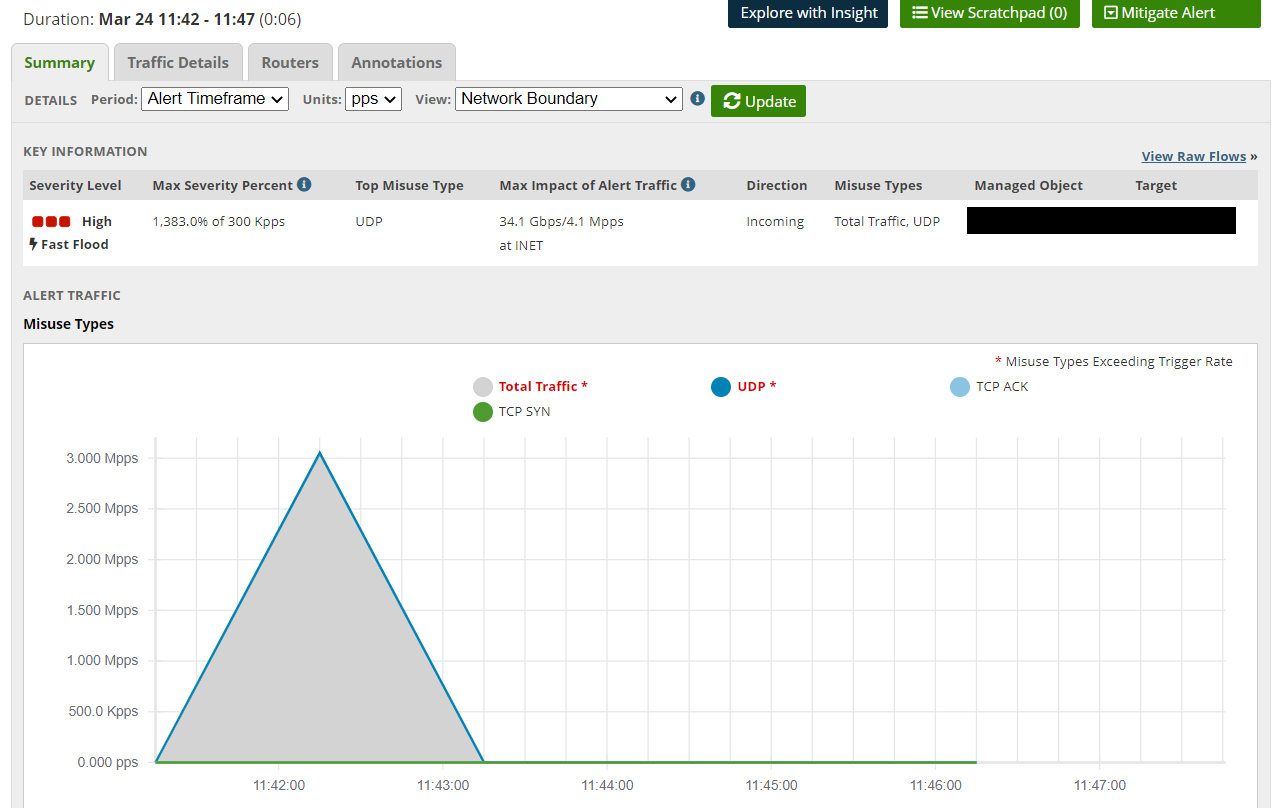
Figure 1:In this top portion of the DoS Alert Summary Report, we see bps and pps levels are indicative of unusual traffic
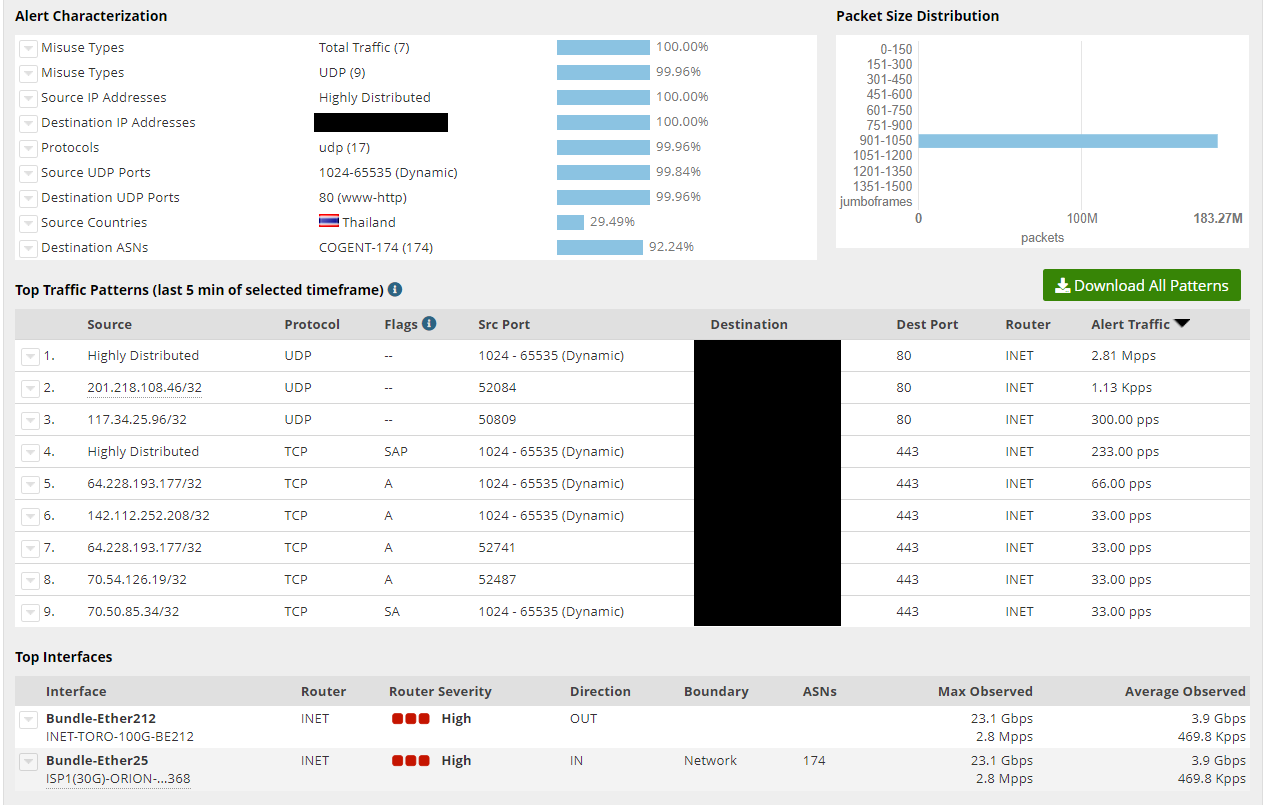
Figure 2: In this bottom portion of the DoS Alert Summary Report, we can identify the type of misuse or attack and its source
In Figure 2, above, the DoS Alert Summary Report details the alert characterization, including the source information. It explains how this DoS event was identified as a user datagram protocol (UDP) flood (misuse type) and what source IPs were used to inject this traffic. An event is a DDoS that is targeting one or more IPs from multiple source IPs and ports. The Figure 2 shows that this particular event was a DDoS incident. In order to help mitigate this attack, ORION dissected the incident to identify the potential bad actors.
The relationship diagram in Figure 3 shows a comprehensive view of the flow of the DDoS incident as well as details on how the DDoS traffic originated and where the attack traffic came from (source country, Autonomous System Number or ASN, IP and port). While these attributes individually may not help bring out the actual bad actors, when viewing them in combination and understanding where the main chunk of the traffic came from, we have good forensic evidence on what caused the DDoS traffic and how it could be blocked.
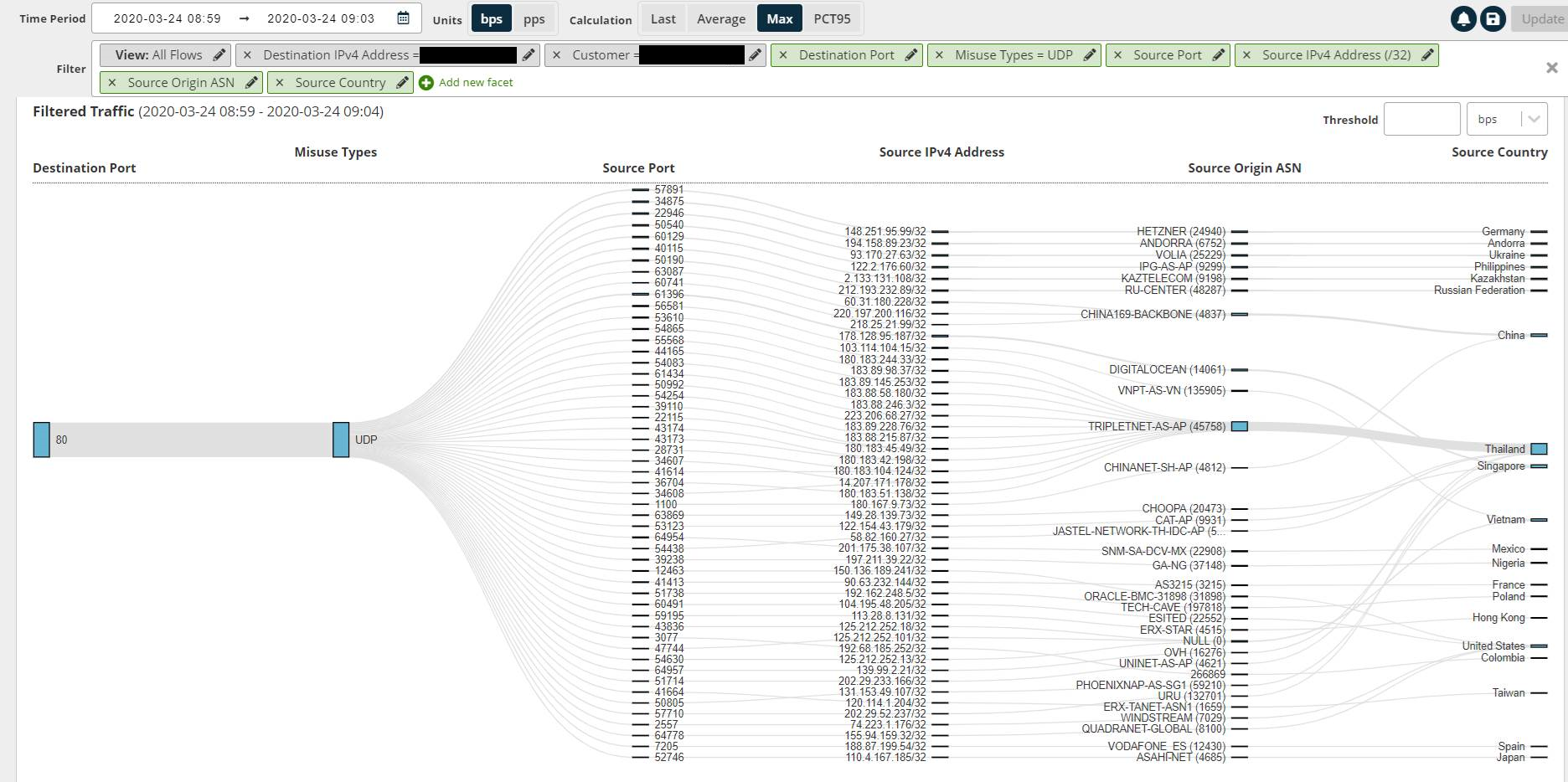
Figure 3: The relationship diagram shows a comprehensive view of the flow of the DDoS incident as well as details on how and where the DDoS attack traffic originated
Looking at the source ports, it is clear that most of the ones used in this attack were unassigned ports. We identified a couple of them – 1100 and 3077, which are known for use in online gaming. Based on most reported DDoS incidents worldwide, we know that one of the most common sources of a DDoS attack is from online gaming. So now we have an indication that there were some applications being used which might have triggered this attack. The high distribution of IP addresses and uniformity of traffic load from each of them indicates, this attack was driven by bots or botnets. These source IPs were most probably not legitimate attackers, but compromised systems that were used to generate this attack traffic. Going further back in the flow, we see that the source ASN and source countries have a thicker band from Thailand and TRIPLETNET-AS-AP ASN. This might indicate that the original attacker belonged to this ISP. However, this can never be confirmed as attackers would use different ways of camouflage.
The forensic content derived from such relationship diagrams can be used by the target’s IT and cybersecurity team to add some well-defined rules and policies in their firewalls or Intrusion Detection System (IDS) that can effectively block or attempt to block such traffic in future. Blocking any traffic from unknown source ports towards the destination port 80 of the target IP could help prevent future attacks. One might also blacklist source ASNs which contributed to major portions of the DDoS traffic. These details can also help build auto-mitigation countermeasures that can automatically identify similar traffic and scrub out the bad components before any impact is felt by the target institution. Overall, such details on any DDoS traffic give IT and cybersecurity teams more power and capabilities to properly investigate, analyse and take action.
Why having DDoS threat protection is important
Education institutions could expect an increase in security events as they shift more and more to remote research and learning. Over the past couple of months and for the foreseeable future, students and faculty are relying on the Internet to submit and grade assignments, conduct testing, collaborate on projects, share research and complete other vital tasks during the academic year.
These organizations are susceptible to DDoS attacks because of their many connections to and data transactions with other institutions around the world. A major challenge is differentiating legitimate traffic from harmful traffic.
If an attack is constructed well, it can mimic normalcy and come across initially as legitimate traffic, making it difficult to identify in the early stages, thereby allowing more time in which to cause damage.
DDoS threat protection helps fortify your network to reduce outages caused by DDoS attacks that can significantly damage your organization’s operation, reputation, and even bottom line.
What ORION offers its constituents
ORION’s commitment
Providing ORION DDoS Threat Protection to all ORION constituents Monday to Friday, 9 a.m. to 5 p.m. is part of our ongoing commitment to robust and reliable digital infrastructure. We are continually upgrading our network and enhancing our services to effectively respond to the changing needs of our constituents and the global threat landscape.
How ORION DDoS Threat Protection works
ORION’s “alert, assess, address” service model enables us to provide high-quality protection to help avoid breaches which can cripple your network and cause expensive downtime.
- Alert – Identify suspicious traffic that could cause denial-of-service by using a powerful cybersecurity system
- Assess – Monitor Monday-Friday 9-5 and detect attacks in the network before they can reach your systems
- Address – Get comprehensive incident reports and an annual summary of all DDoS alerts while we together take the necessary steps using the reports and data to effectively stop DDoS events
ORION’s inline system detects and stops threats targeting your network with no additional on-site equipment, software, or intervention required. Now, your staff and network can stay focused on your core business and leave the gory details to us.
For more information on ORION’s DDoS Threat Protection, visit: https://www.orion.on.ca/about-us/orion-ddos-threat-protection/ or contact the ORION team at communitydev@orion.on.ca

